PRODUCT
& SERVICE
SAP (NETWORK FORENSIC) PatronuX > Product & Service > Threat Intelligence
The life of a packet (The Competition)
- DMA
from NIC to
memory - Wrapped
in SKB - Sent to
networking
stack - Copied to
user-space - Copied to file
system, back to
kernel-space - DMA from
“page cache”
to Disk
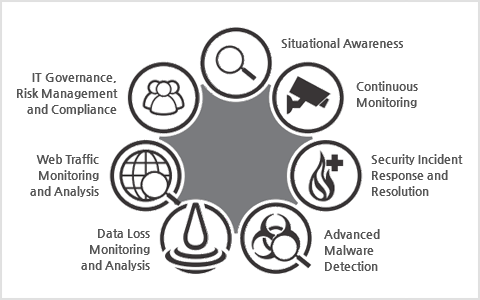
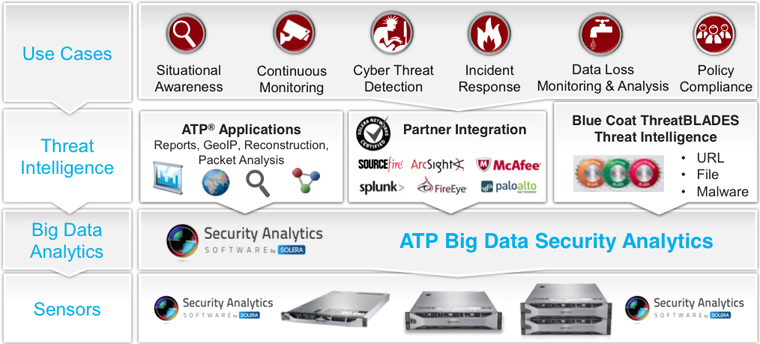
네트워크 트래픽의 Big Data를 분석하여 통합된 위협을 예측 및 탐지하고 대응할 수 있는 체계를 수립할 수 있습니다.
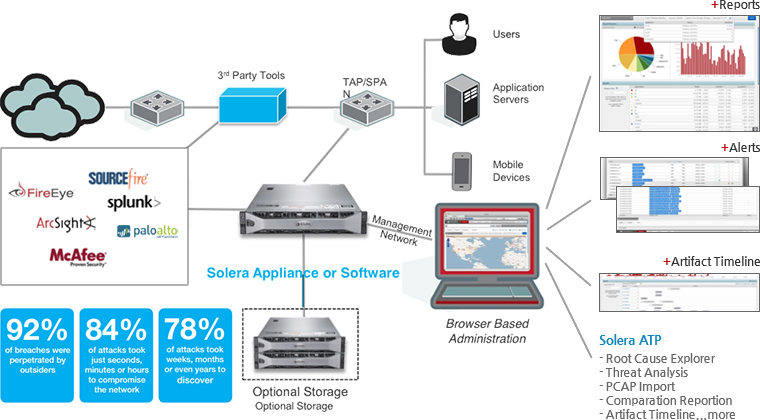
- 전체 트래픽 완벽 캡쳐 및 자체 분석 엔진을 통한 전체 Application에 대한 가시성 제공
- 독립적 운영(Appliance)으로 기존 네트워크에 영향이 없으며, 분산 환경에서도 트래픽 수집 및 분석
- 전체적인 상황 인식 및 근원 분석 제공
- 실시간 모니터링을 통한 데이터 유출 방지 및 보안 준수
주요 기능
LAYER 2 TO 7 ANALYTICS
- 네트워크 전체 패킷에 대하여 분석
전체 세션 재구성, 데이터 시각화, IP 위치 및 추적, 패킷 분석, 타임 라인 분석, 동향 분석, 파일 및 객체 재구성 등
REAL TIME INTELLIGENCE
- 추출기(Extractor) 실시간 분석
파일 및 네트워크 흐름을 실시간으로 추출하여 즉시 재구성과 분석을 통하여 위협을 탐지
APPLICATION CLASSIFICATION
- 분류를 통한 시각화 및 통계
네트워크로 유입되는 패킷을 대상으로 콘텐츠 형식, 파일 이름, 프로토콜, 2,200 가지의 프로그램과 수 천 개의 설명 메타데이터
속성 등을 쉽게 분석하기 위한 분류
CONTEXT-AWARE SECURITY
- 상관 분석
전체 패킷을 분석하고 분류하여 특정 객체를 대상으로 유입경로, 유입IP, 프로토콜, 프로그램, 파일 등 다양하게 분석
ROOT CAUSE EXPLORER
- 근본 원인
추출기를 통하여 의심스러운 웹 세션, 이 메일 등을 객체를 사용 근본 원인을 분석
주요 분석
- 확장 용이, 중앙 관리
- Web base 운영관리 (멀티브라우저 지원)
- 10G 지원 및 고 용량 처리
- 독립적 구축, 전체 기능 built-in
- 사전 설치 및 구성된 솔루션
- 대용량 파일시스템 지원(특허)
- Appliance, S/W, VM 환경 지원
주요 레퍼런스